Connection Proxy
The connection proxy is a new role in the Kasm Workspaces architecture as of version 1.12.0. The connection proxy role server is responsible for translating connection types that are not web native, into an HTML5 accessible connection. Support connection types include RDP (to include RDS), SSH, and VNC protocols. The underlying technology powering this role is a custom build of Apache guacd and a Kasm connection management service that is responsible for Kasm customized integration with guacd.
Notably, the Connection Proxy can achieve local load balancing by spawning multiple instances of the connection management service, each running on a separate core, all within the same container. The number of instances to spawn can be controlled by using the installation parameter “–guac-cluster-size N”, where N signifies the number of instances you wish to create. In the absence of this parameter, the system defaults to creating as many instances as there are cores on the system.
Architecture
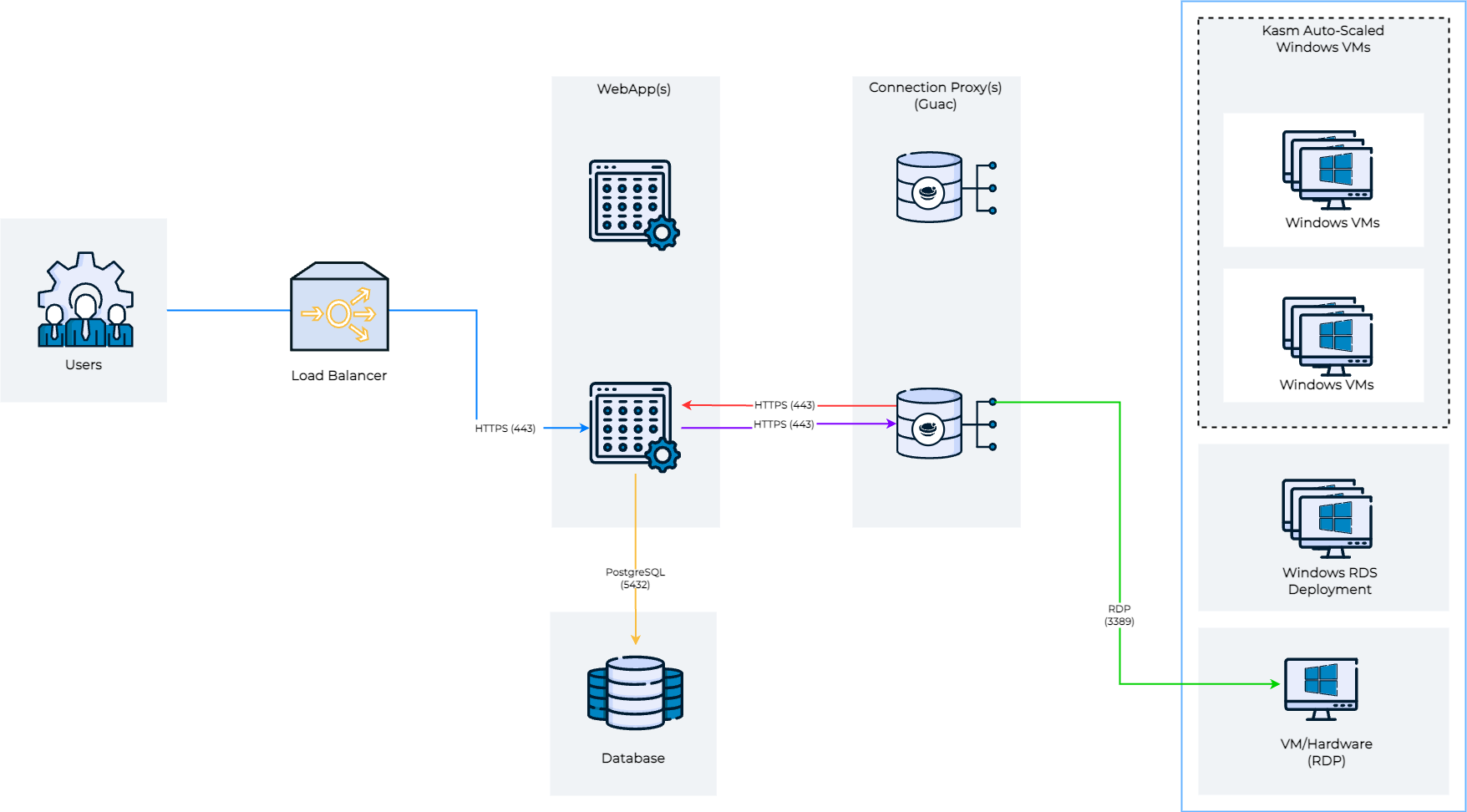
Architecture
The above diagram shows the architecture and user flow of traffic. When a user connects to a remote session comes in, shown in blue, the request can optionally be load balanced between multiple web app servers. The Web App server queries the database for a list of potential connection proxy servers that are responsible for the Kasm Deployment Zone that the requested server is in. The Web App service goes down the list of connection proxies in random order and performs a health check. The user’s HTTPS connection is then proxied to the first connection proxy server (purple line), in the request zone, that responds to the health check. This sequence of events ensures resiliency in the event of networking or server issues with a single connection proxy.
When the HTTPS connection from the user enters the connection proxy, the connection proxy performs an authentication request up to the Web App Role server (red line) to authenticate the user, authorize that the user has access to the requested server, and to download connection details for the server. The connection proxy then performs an RDP connection to the remove server (green line) and performs the translation from RDP to a web native format for the end-user.
Single server deployments have all roles installed on a single server. For multi-server deployments, you should consider deploying at least 2 connection proxy servers per Kasm deployment zone. Kasm will automatically load balance users and provide automatic fail-over should one stop responding.