Why Enterprise Browsers?
The Browser is the Application
In 1995, the first commercial internet browser started taking shape. Within one year, the browser wars began. By 2000, corporations took advantage of the benefits of the browser, shifted away from applications installed on desktops, and began webifying their applications.
Today more than 93% of all corporate activity is done through an internet browser. We know the names: Chrome, Safari, Firefox, MS Edge, and Opera to name a few.
Schedule a Call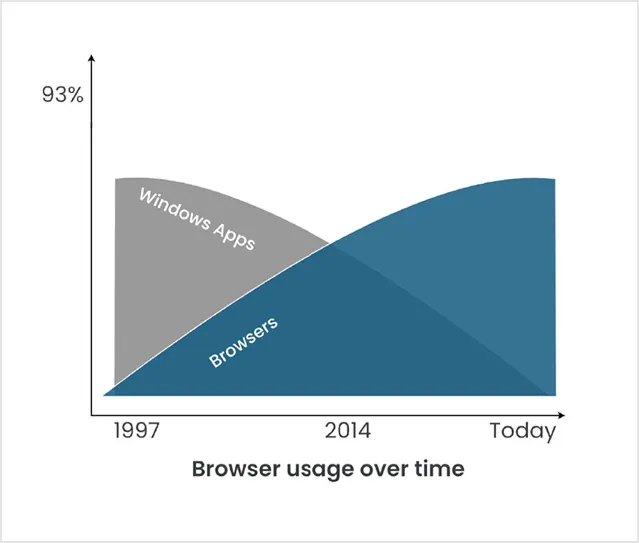
Our motto “SAY YES” to new security techniques and corporate compliance.
Old ways are
Hard to change
Our IT departments work diligently to protect their internal customers’ work products from attacks that come from many angles. Many hackers are technology experts and make it their business to find new ways, or vulnerabilities, to use to attack end users on their devices.
Internet
Network
Laptop
WiFi
Office
Browse
Device
For a hybrid worker, their laptop is everything. This makes it highly susceptible to being targeted by attackers. The same defense models from the 1990s are still the ones in use today. The threats are increasingly web-based and use social engineering to bypass security controls.
Browsers
Once a browser allows in the malicious code, the potential to spread to the endpoint and across the network is very high. However, locking down the browser causes numerous other problems. A balance must be reached within corporations; use the browser, but use it carefully.
Monitor for attack, "if found" delete it, get a new patch to monitor the next attack.
"If found" are the two words everyone lives by today. With today's collaborative workplaces, it only takes a matter of minutes for a virus to infect the whole organization if not protected. As the attackers become more savvy, malware is programmed to wait for the opportune moment to cause the most damage..destroying systems, leaking data and bringing down whole corporations.
There is a Better Way
Our “Virtual Browsing” remote container strategy isolates activity away from the device and securely accesses it from the cloud.
Your virtual browsing activities are securely streamed to your local browser. No worries about compromising your local device. No worries about infecting the corporate network. Malware has no place to go. It is isolated in the container. Your data stays safe.
Feel safe blending work and personal browsing activities on your device.


We believe
Containers have Super Powers
Do you want to access your data or do you want to protect it?
Many existing remote access systems are designed with access architecture at their core. In the 1990s, that was necessary. However in todays worlds, it creates opportunities for hackers, malware, and data theft.
At Kasm, the container approach, steeped in security, makes for a winning combination between access and protection.
“Say Yes to Both – Access and Protection!”
Armed with Virtual Browsing, your end user’s devices are safe. IT no longer has to worry about end user’s getting hacked and their corporate environment infected. The Enterprise Browser has cybersecurity features built-in.
Say Yes to Both - Access and Protection!
Secure Access
- Single-Sign-On Identity Access Management
- Zero-day Vulnerability Mitigation
- Rate Limiting for DDOS prevention
- HTTPS Encryption with SSL/TLS
Active Protections
- Web Application Firewall (WAF)
- Zero-day Vulnerability Mitigation
- Advanced Rate Limiting for DDoS protection
- Nightly Builds to Automate Patching/Upgrades

Looking for a Customized Solution?
Explore how Kasm Workplaces can enable your web-native remote workspaces.
Contact Us

